Tokyo Tsushin Kogyo is one of the oldest companies in the tech world. It was founded after World War II, repairing radios and inventing household appliances—including a failed electric rice cooker. Because its name was too complicated for Western markets, it changed it to something simpler: Sony.
This article isn’t about the company’s legacy of innovation. It’s about a major blunder from just 20 years ago—arguably the biggest mistake in Sony’s history: installing malware on its music CDs.
Oh, the MP3. While the MP3 format exploded in popularity in the late 1990s and early 2000s, its roots go back much further. In the 1980s, German engineer Karlheinz Brandenburg developed a way to compress digital audio files so that the loss in quality was imperceptible to the human ear.
Free Lossless Audio Codec purists may insist MP3 is the devil, but Brandenburg’s team built an algorithm that eliminated sound data the human ear can’t easily detect. The result? File sizes shrank dramatically. This revolutionized consumer tech: portable MP3 players hit the market, digital music distribution took off—and so did song copying and illegal downloads.
On the attack. By the early 2000s, Sony Music had become a giant in the recording industry. Today, the company fiercely critiques AI developments, but back then, MP3 was the big threat—and Sony was ruthless in its response.
In August 2000, Steve Heckler, vice president of Sony Pictures Entertainment, made it clear:
“The [music] industry will take whatever steps it needs to protect itself and protect its revenue streams. It will not lose that revenue stream, no matter what.”
Aggressive, indeed. Heckler even said they would firewall Napster:
“We will develop technology that transcends the individual user. We will firewall Napster at source. We will block it at your cable company, we will block it at your phone company, we will block it at your [Internet-service provider]. We will firewall it at your PC.”
And Sony followed through.
XCP. Not long after Heckler’s comments, Sony released Natalie Imbruglia’s second album with copy protection—but didn’t announce it. This wasn’t a one-off: The company released several albums in specific markets with similar protection systems. Before its merger with Sony, BMG also shipped millions of albums with digital rights management (DRM).
In March 2004, Sony and BMG formed a 50-50 alliance, flexing their muscle in the music industry. Both companies had taken a hardline stance against piracy and hired a company called First 4 Internet to help.
The solution? Extended Copy Protection (XCP). When you inserted a music CD with XCP into a PC, the autorun function launched and displayed a license agreement. If users declined, the CD would eject and wouldn’t play. If they accepted, they could enjoy the music—but copying was limited to three duplicates of the full CD or three copies per track.
Some eye-popping items from that End User License Agreement (EULA):
- If you moved to another country, you had to delete your music—even if your CD was stolen.
- You agreed that Sony could install backdoors on your PC to protect its rights.
- You couldn’t sue Sony for more than $5.
But the worst part wasn’t in the fine print.
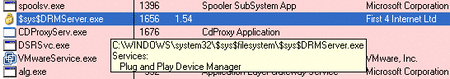
It was malware. Accepting the EULA didn’t just unlock the music. It also installed several programs—Sony’s proprietary player, audio drivers, and the DRM itself. Hidden among these was something more insidious: a rootkit called “$sys$aries,” which activated on startup and hid its processes, even from antivirus software.
This left a massive security hole in users’ systems—one that malware could easily exploit.
Busted. In October 2005, software engineer Mark Russinovich published a blog post exposing the rootkit. He explained how it worked, accused Sony of going too far with DRM, and pointed out that the EULA never mentioned the hidden software.
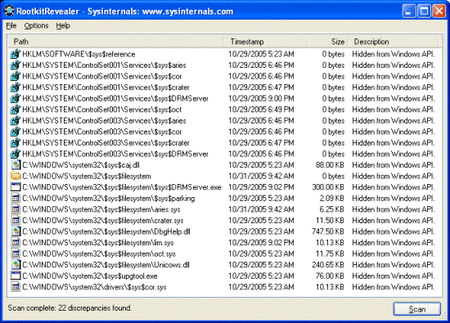
Russinovich wasn’t some random blogger. The Spanish-born American engineer is now the CTO of Microsoft Azure. He also uncovered a similar rootkit in Norton software in 2006. In this case, he showed that Sony’s rootkit used insecure methods, could lead to system crashes, and was nearly impossible to uninstall. Even when no Sony CD was playing, the software consumed resources in the background, slowing down PCs.
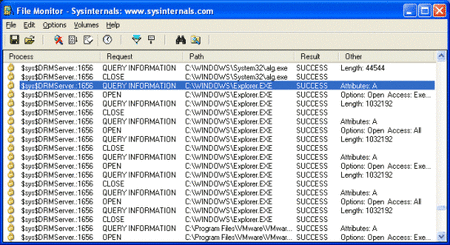
Reaction. Sony initially denied the accusations but quickly released a removal tool. The problem? It didn’t work. Russinovich tested the patch and found that it simply revealed the hidden files—it didn’t remove the rootkit.
Worse, the tool installed even more software, which couldn’t be uninstalled unless users downloaded a separate file after submitting their email address to Sony. Microsoft had to release security patches. This wasn’t just a user nightmare—it was a PR disaster.
The consequences. In November 2005, Sony BMG finally released a tool that fully removed the rootkit. But by then, the damage had been done. About 22 million CDs with XCP had already been distributed. Sony began pulling unsold units and allowed users to exchange affected discs for clean versions. Security experts warned consumers not to install any software from CDs—especially music CDs, which shouldn’t contain executables in the first place.
That same month, the state of Texas sued Sony BMG for installing spyware. Attorney General Greg Abbott said, “Thousands of Texans are now potential victims of this deceptive game Sony played with consumers for its own purposes.” Sony was forced to pay $750,000 in legal fees, refund customers, add warnings to CDs, and pay up to $150 per damaged computer.
Other states and countries, including Italy and the U.S. Federal Trade Commission, joined the wave of lawsuits and investigations. Even cybercriminals took note of how the rootkit concealed itself, applying similar techniques to their own malware.
Apple was very happy. Sony wasn’t the only label pushing DRM, but it was the most aggressive. That gave Apple an opening. While major labels restricted legal copying for MP3 players, iTunes offered simple access to digital music. iPod owners flocked to the platform.
Labels clung to DRM until 2007, when EMI, Vivendi, and Warner finally abandoned it. Sony BMG followed in 2008, hoping to revive sales through platforms like Amazon and regain market share lost to Apple. However, the rootkit scandal’s damage lingered. In October 2008, the Sony-BMG alliance dissolved.
Sony Music reemerged under its original name. Despite the scandal, it grew into the powerhouse it is today, now rivaling Universal and Warner Music.
Images | Manuel bonadeo (Unsplash) | Mark Russinovich



